Tools and Equipment Used:
- Samsung Galaxy Grand Prime - Rooted - Android 5.1.1 - Microsoft Cortana Digital Assistant - 2.10.5.2209 enus release (updated on May 31st, 2018) - Forensic Imaging: Magnet Acquire 2.4.0.11694 - Forensic Image Processing: Autopsy 4.7.0 - SQLite Viewer: Forensic Browser for SQLite 3.2.14 Summary: Cortana keeps a variety of pertinent information about the user and their activities including geolocations, timestamps, user history, known devices, and events/reminders among other data.
DssDatabase: - Location: /userdata/data/com.microsoft.cortana/databases/DssDatabase - “Alarmdescriptor” and “reminderdescriptor” - Information about the alarms and reminders set (types: triggerless, location, or time, status last updated times, etc).
- “Notificationdescriptor”
- Notification information, in this case News and Weather. Both include the content, links,
notification time and other data.
- Notably, Weather includes the location (i.e the city and state) of the weather you are asking for.
- “Signals” - Latitude and longitude of the device and the timestamp of the location.
RKStorage: - Location: /userdata/data/com.microsoft.cortana/databases/RKStorage - “CatalystLocalStorage”
- User history (the most recent commands the user has given Cortana) - UpcomingStorageCachedTestDataKey where you can see some information on upcoming
calendar events, reminders, to-do list items, weather, and news.
com.microsoft.cortana_preferences.xml: - Location: /userdata/data/com.microsoft.cortana/shared_prefs/com.microsoft.cortana_preferences.xml
- Useful syncing and accessing times (ex. The past 15 days the user has accessed Cortana) - A complete list of the items in the default category to-do list. - The user agent string. Extended: Cortana is Microsoft’s personalized digital assistant, capable of doing a multitude of tasks for the user such as setting reminders, tracking packages, finding facts through internet searches, and sending emails. Cortana has become very popular by allowing it's users to get certain tasks done quickly, easily, and most importantly hands-free. However, Cortana leaves logs that allow forensic experts to gather information about the users' history such as location, searches, weather, and etc. Even after disabling some settings, Cortana can still keep logs of data that can be potentially used by investigators. Procedures The first step was to download Cortana from the Google Play Store on to my rooted Android device (Samsung Galaxy Grand Prime).



- Samsung Galaxy Grand Prime - Rooted - Android 5.1.1 - Microsoft Cortana Digital Assistant - 2.10.5.2209 enus release (updated on May 31st, 2018) - Forensic Imaging: Magnet Acquire 2.4.0.11694 - Forensic Image Processing: Autopsy 4.7.0 - SQLite Viewer: Forensic Browser for SQLite 3.2.14 Summary: Cortana keeps a variety of pertinent information about the user and their activities including geolocations, timestamps, user history, known devices, and events/reminders among other data.
DssDatabase: - Location: /userdata/data/com.microsoft.cortana/databases/DssDatabase - “Alarmdescriptor” and “reminderdescriptor” - Information about the alarms and reminders set (types: triggerless, location, or time, status last updated times, etc).
- “Notificationdescriptor”
- Notification information, in this case News and Weather. Both include the content, links,
notification time and other data.
- Notably, Weather includes the location (i.e the city and state) of the weather you are asking for.
- “Signals” - Latitude and longitude of the device and the timestamp of the location.
RKStorage: - Location: /userdata/data/com.microsoft.cortana/databases/RKStorage - “CatalystLocalStorage”
- User history (the most recent commands the user has given Cortana) - UpcomingStorageCachedTestDataKey where you can see some information on upcoming
calendar events, reminders, to-do list items, weather, and news.
com.microsoft.cortana_preferences.xml: - Location: /userdata/data/com.microsoft.cortana/shared_prefs/com.microsoft.cortana_preferences.xml
- Useful syncing and accessing times (ex. The past 15 days the user has accessed Cortana) - A complete list of the items in the default category to-do list. - The user agent string. Extended: Cortana is Microsoft’s personalized digital assistant, capable of doing a multitude of tasks for the user such as setting reminders, tracking packages, finding facts through internet searches, and sending emails. Cortana has become very popular by allowing it's users to get certain tasks done quickly, easily, and most importantly hands-free. However, Cortana leaves logs that allow forensic experts to gather information about the users' history such as location, searches, weather, and etc. Even after disabling some settings, Cortana can still keep logs of data that can be potentially used by investigators. Procedures The first step was to download Cortana from the Google Play Store on to my rooted Android device (Samsung Galaxy Grand Prime).
Cortana has over 30,000 downloads on Android phones
After downloading, you have to set up a Microsoft account or log in if you already have one, and from there I created a multitude of test data. Some examples of the test data I created are:
“Weather today”
“Top news?”
“Convert 1866 kb to GB”
Set 'Random Reminder'
Added calendar event 'Grandma’s Birthday'
I created a physical image of the Android device using Magnet Acquire, and for analyzing I used Autopsy. Both are free amazing forensic software tools - found here for Magnet Acquire, and here for Autopsy.
Database Analysis
Using Autopsy navigate to /userdata/data/com.microsoft.cortana/databases/
Inside databases, there are 5 different SQLite databases listed, DssDatabase, AriaStorage, ial_en-us, RKStorage, and sql_preferences. The ones that are of the most interest are the DssDatabase and RKStorage databases.
The directory structure of com.microsoft.cortana (left) and the contents of the databases folder under where these SQLite databases can be found (right).
DssDatabase notably contains all information on alarms, reminders, notifications, and signals from the device.
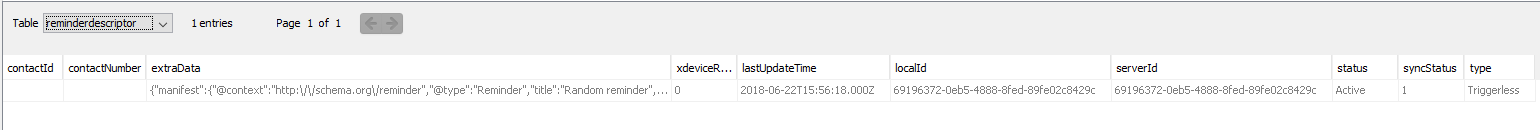
- “Alarmdescriptor” and “reminderdescriptor” tables contain information about the alarms and reminders set. Worth mentioning is the update time and the active status in the reminder descriptor, and the last wake up time in the alarm descriptor.
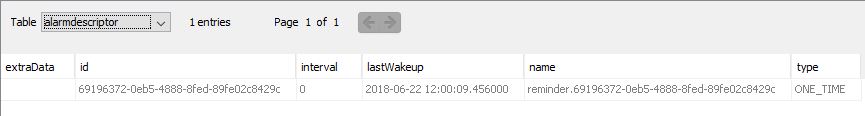

DssDatabase’s alarm descriptor table.
Reminder descriptor table.
Seeing what appears to be relevant information stuffed into the reminder descriptor table under the extra-data column, I extracted the databases I wanted from Autopsy and opened them using the Forensic Browser for SQLite (found here) to view the data more clearly. From there I copied the columns I wanted to examine further and put them in their own text document.
Using Alexis Brignoni's Discord-JSON-chat-conversions parser (found here) I was able to take the JSON formatted extra-data column (put into its own text document) from reminder descriptor and convert it into a more user-friendly HTML page. The tool made it was easier to read all of the reminders the user has created. I could even see that there was a recovered deleted reminder that was stored there! For each reminder, the table listed items such as the last updated time, last viewed time, if and when it was completed, and if there were any files attached to it. If there were attached files, the tool would list their names.
The completed reminder titled “Random Reminder” formatted in HTML.
Side Note: From this, I took the image file’s name, keyword searched it in Autopsy, and was able to find the image that was attached to this old reminder.
- “Notificationdescriptor” table includes notification information - in this case News and Weather. Both include the content, links, notification time and other data. Notably, Weather includes the location (i.e the city and state) of the place you are asking for.
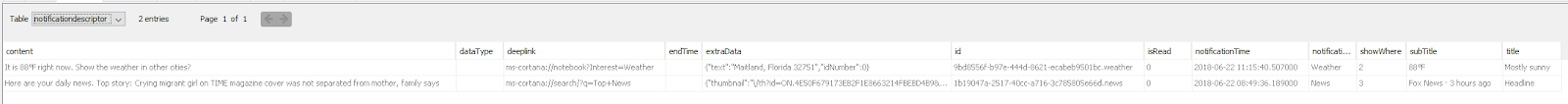


Notification descriptor with listed Weather and News.
- “Signals” table contains latitude and longitude of the device and the timestamp of the location. Upon further research it shows Cortana sends a signal at what appears to be a random interval, but I have only ever found signals stored here for the given day. Further research would be needed to conclude if it actually does reset daily, and if those signals get pushed to Microsoft or what happens to them.
Signals with censored latitude and longitude location - Now you can’t know where I’m at! Ha
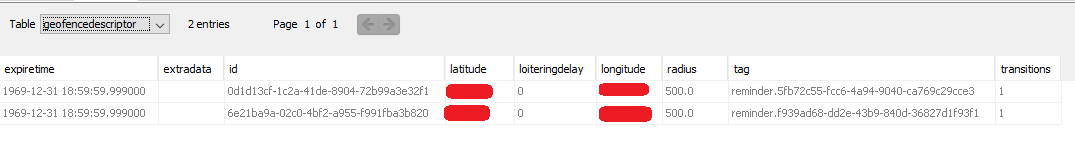
- “Geofencedescriptor” table also contains the latitude and longitude but only for two reminders that were set with a location reminder. There would need to be further testing to conclude if these are the only type of items stored here.
Geofence descriptor reminder information.
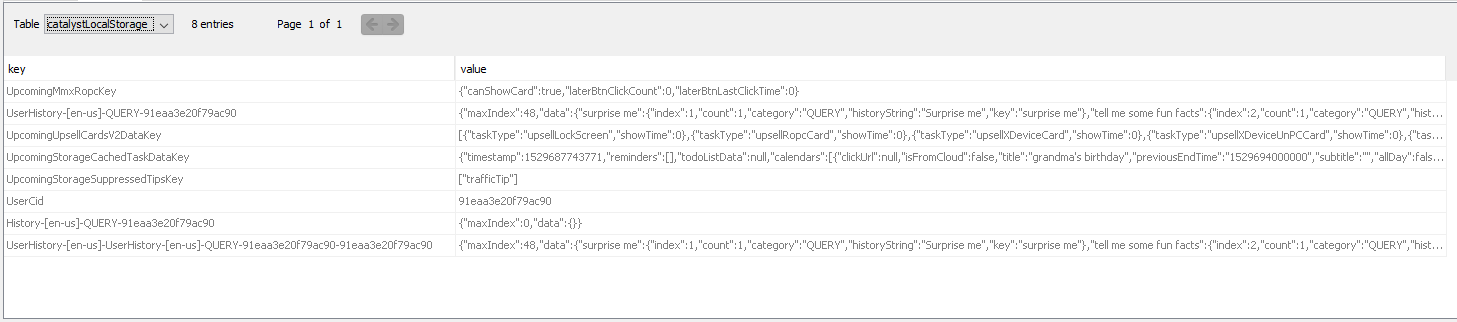
Within the RKStorage database there is a table called “catalystLocalStorage” which contains the user history (many recent commands the user has given Cortana) and other useful data such as upcomingStorageCachedTestDataKey where you can see some information on upcoming calendar events, reminders, to-do list items, weather, and news.
Preview of the upcomingStorageCachedTestDataKey table
Using Brignoni’s python script again, I converted the JSON formatted value columns for UserHistory-[en-us]-QUERY-91eaa3e20f79ac90, UserHistory-[en-us]-QUERY-91eaa3e20f79ac90-91eaa3e20f79ac90, and UpcomingStorageCachedTaskDataKey into a prettier HTML format.
Without converting the JSON key-values into HTML it is hard to detect any difference between the two user histories, but with the HTML I found that the user history with the appended “91eaa3e20f79ac90” twice has a couple more history entries than the first. It also shows the correct order in which the questions were asked Cortana, with index 1 being the oldest.
UserHistory-[en-us]-QUERY-91eaa3e20f79ac90 is pictured left and UserHistory-[en-us]-QUERY-91eaa3e20f79ac90-91eaa3e20f79ac90 right
It also appears to show the amount of times a user asked the question with the count accurately reflecting the test data inputted on the device.
The upcomingStorageCachedTestDataKey was also converted into HTML and does not contain the full list of all items created for calendar, reminders, and to-do items. The to-do list items mentioned are also only ones from the “default category” to-do list. It also only appears to show only the most recent or upcoming items, but further research would be needed to confirm.
Other Artifacts
Still in the /userdata/data/com.microsoft.cortana/ directory there is a folder called app_webview that contains the Cookies database and another folder called IndexedDB.
In Cookies there lists some past websites the user has accessed through cortana. In IndexedDB there is a folder called https_tpc.googlesyndication.com_0.indexedddb.lebeldb where I found some recovered images.
At /userdata/data/com.microsoft.cortana/shared_prefs there is a file titled com.microsoft.cortana_preferences.xml. Since it is an XML file you can easily extract it and open it in a web browser. Here there appears to be much more than just the user’s preferences.
There is a multitude of times listed for all sorts of actions such as List Data Sync Time, Last Log Time, and even what appears to be the last 15 days listed for when Cortana was launched (Although more research would be needed to confirm it).
Presumably, the last dates Cortana was launched
There is also a complete list of the the items in the default category to-do list, which is the only complete list I found.
Default category to-do list items.
This is the only file where I have found the other lists that I have created even mentioned, although I haven’t found any of their items listed.
I'd love to hear suggestions and comments on how I can improve my research and knowledge in cyber security.
Comments
Post a Comment